Cisco Investments launched the 2023 CISO Survival Guide with top VCs to uncover priorities and future trends in cybersecurity.
CISOs prioritize identity and access management, with demand for unified IAM, IGA, PAM, and emerging CIEM platforms.
Cloud security must evolve beyond prevention, with CNAPP bridging pre- and post-breach protection.
Cybersecurity sits at the crossroads of a worldwide digital reassessment. The tools that got us through pre-pandemic times will not sustain security going forward.
CISOs face tough decisions as they are challenged with securing sensitive enterprise applications and provisioning dynamic user access in the backdrop of myriad enterprise collaboration tools, remote/hybrid work, and lengthening supply chains.
Motivated by the question of “what’s next?” this year’s CISO Survival Guide was authored by Cisco Investments in conjunction with cybersecurity-focused venture capitalists within the startup landscape: Forgepoint Capital, NightDragon, and Team8. We set out to address the heart of that very question:
What’s next?
To do this, we listened to customers, CISOs, innovators, startup founders, and other cybersecurity experts to gain a comprehensive understanding of their challenges and priorities. While each VC tackled the problem from a different angle, unification was the one theme that cut through it all. They need more interoperability and less friction. And they demand more decipherable data when making the decisions that count.
Key Priorities Uncovered
Cisco Investments, in our research, found that an overwhelming majority, 85%, of IT decision-makers are prioritizing Identity and Access Management investments more highly than other security solutions. But – related to this – CISOs clearly voiced their critical pain point: The lack of a singular platform across Identity Management (IAM), Identity Governance and Administration (IGA), and Privileged Access Management (PAM). Enterprise and workforce identity is a singular problem that should eventually be solved on a single, unifying platform. Another key takeaway is the strong emergence of Cloud Infrastructure Entitlements Management (CIEM) to simplify and secure operations in the cloud.
In addition, Cloud Security sits at the top of CISOs’ priority list. However, Team8 investigations revealed that current Cloud Security tools are primarily preventative in nature, addressing the 'left of boom.’ Team8 postures that the Cloud Native Application Protection Platform will bridge left of boom and right of boom, post breach, providing an all-inclusive platform that prevents, detects and remediates.

Forgepoint noted that CISOs are no longer tasked with security alone, but rather are accountable for ensuring that security enables and empowers business operations. According to Gartner, 88% already recognize that cybersecurity poses a risk to the business, and 64% of board directors increasingly emphasize digital assets. That’s why Forgepoint maintains that controlling access to information remains the crux of cybersecurity, with Data Identity and Privileged Access Management (PAM) being a top priority for CISOs. They note that Data Security represents yet another hub category with many spokes, including Data Access Control and Data Loss Prevention.
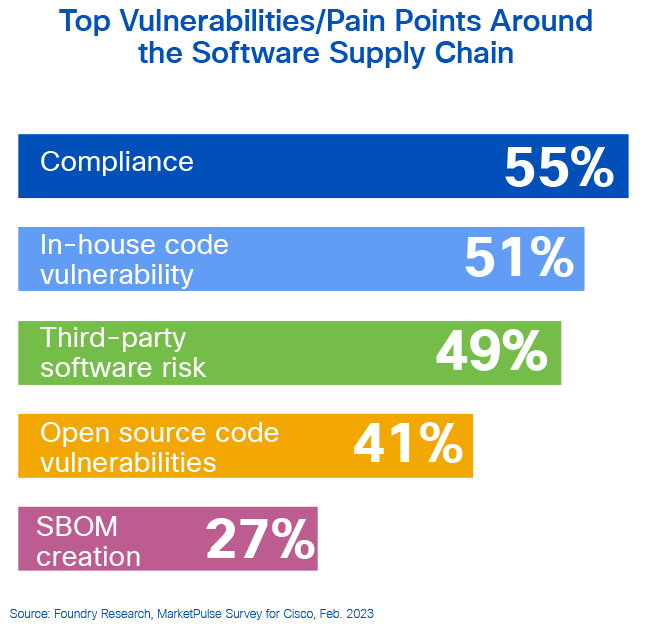
Taking things back a step, the systems that secure data are only as safe as their code. NightDragon emphasizes that the software supply chain is the weakest link in an enterprise, thanks to agile DevOps and a more rapid development lifecycle. This makes visibility a challenge and governance a chore, with 55% of respondents placing compliance among their top three software supply chain concerns. Companies must create a holistic software supply chain strategy to manage the load. Ultimately, this involves managing OS code, the delivery pipeline, and third-party software – again, in a unified approach. The cybersecurity industry is at an inflection point with dynamic evolutions in all layers: SASE, Zero Trust, CNAPP, DSPM, SSPM, DRPS...A focus on core use cases (such as adaptive application access, privileged identity, or developer access) and demonstrate differentiation on functional axes (such as ease of deployment, breadth of coverage, rich integrations, etc.) is becoming more critical than ever.
So Much More
What you’ve read is just a taste of the rich insights and telemetry that the 2023 CISO Survival Guide offers. In reading the full depth of the guide, I hope that you find new perspectives to your pressing security challenges.
See how startup trends will impact the cybersecurity landscape in the year ahead.

